Up to 87% of organisations now consider video to be a core technology to support business operations, a new Metrigy study has found.
Along with the rise in adoption of video meeting apps comes a need to ensure security of meeting access, content shared within meetings, and meeting archives, says the report called Securing Remote Collaboration: A Primer.
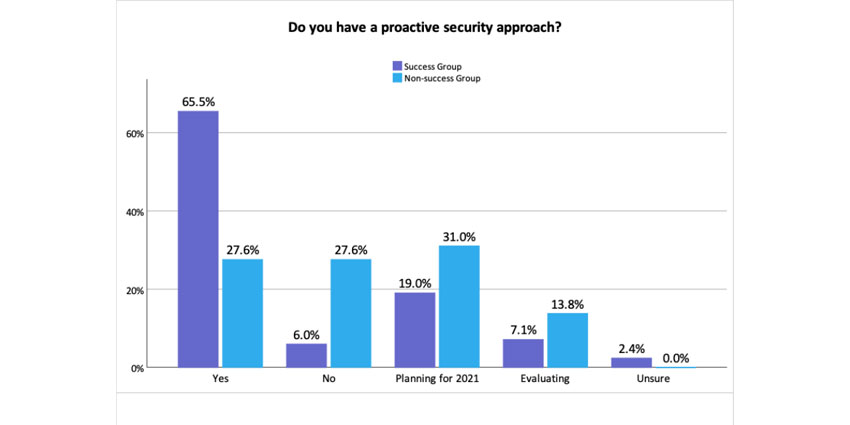
The study follows Metrigy’s Workplace Collaboration: 2021-22 global research of 476 end-user organisations, which revealed that 82% now use video meeting applications for all or most meetings. It also found that 41% of businesses currently use more than one meeting and collaboration application, creating difficulty in ensuring consistent application of security policy across multiple applications. This comes as just 66% of successful companies have a proactive workplace collaboration security strategy.
The report offers up advice for business leaders to ensure meetings are secure and protect against the following common threats:
- Unauthorised meeting access by those who are not permitted to attend a meeting
- Content leakage of chats, transcripts, and content shared within and outside of a meeting
- Data loss from employees inadvertently, or deliberately, sharing confidential, restricted information into meetings such as sensitive files or data
- Attendee privacy protection especially in use cases such as telemedicine and court activities
The report reads: “As a result of growing awareness of security issues, about 55% of companies are increasing their collaboration security spending to include third-party services and platforms to enforce policy and manage compliance.
“Among successful companies, nearly 75% are increasing collaboration security spend. In fact, successful companies are approximately 20% more likely to increase collaboration security spending compared to non-successful companies.”
Metrigy offer up some best practices in the study. Examples include:
- Controlled Access to Meetings and Content: Applications should enable administrators to require authenticated attendee registration using Active Directory Domain Services (ADDS) or another directory or identity management solution. It should also provide attendees with the ability to verify the authenticity of the host
- User Authentication: The application should allow for users to register and join meetings and workspaces, using credentials provided by a trusted Single Sign-On (SSO) authority. Ideally, the SSO should rely on SAML (Security Association Markup Language) to allow for federated identity between the SSO and the collaboration application service provider
- Private Meetings and Virtual Collaboration Spaces: Private meetings and virtual collaboration spaces allow companies to restrict the listing of meetings and spaces in directories and in calendars, providing additional protection against risk of unauthorized access. In addition, meeting applications may enable restrictions against anyone joining a meeting that isn’t specifically invited, using user authentication methods previously discussed
- In-Meeting Security Controls: In-meeting controls include features that meeting organizers can use to monitor meetings (including chat content and file sharing) and enforce appropriate controls. For example, features could require, or block meeting recording, chat, file sharing, screen sharing, camera use, etc. In-meeting controls could also allow meeting hosts to kick out or mute participants who are disruptive and can allow hosts to automatically mute all participants as they arrive
The report concludes: “Collaboration applications are a fundamental cornerstone of collaboration in the modern distributed, virtual, and hybrid enterprise. The rapid adoption of collaboration and meeting apps as a result of the COVID-19 pandemic shift to remote work has created challenges for IT, security, and business leaders to ensure that their use of such apps affords protection from unauthorized access, as well as access to meeting recordings and content.”